I recently came across an XSS vulnerability in the Tamper Data plug-in for Firefox.
Abstract:
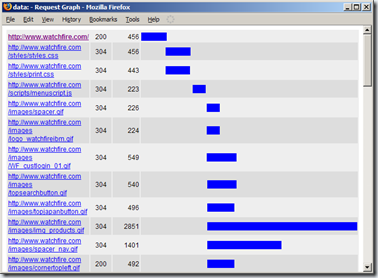
Tamper Data is capable of generating HTML based graphs of request timings. The graph view includes a variety of information about the requests, such as HTTP status, timing, and URL.
Vulnerability:
The displayed URLs are not sanitized before being printed to the output stream, this allows malicious users to inject HTML into the Graph View's DOM.
An attacker can trigger this vulnerability by various methods.
One method might be to convince a naive user to visit a specially crafted URL that contains a malicious script, while Tamper Data is activated.
Another method might be to convince the victim to surf into a site which the attacker controls. The attacker can then make the site cause the victim's browser to initiate a request to a URL which contains HTML of the attacker's choice.
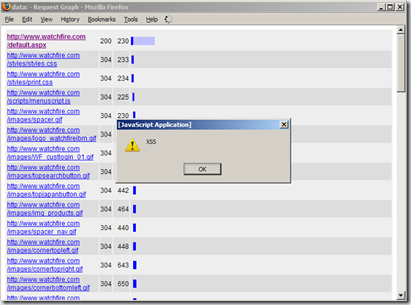
If the victim runs the "Graph All" feature after the malicious URL has been captured by Tamper Data, the attacker's HTML will be rendered in the context of the Graph view's DOM, enabling the attacker to run malicious scripts, as shown below:
Impact:
1) Information Leakage: This vulnerability can be exploited to access data displayed on the victim's Graph View page.
2) Phishing: This vulnerability can be exploited to display false information on the victim's Graph View page.
Test Environment:
Firefox 3.0, Tamper Data 10.0.4
Fix Recommendation:
A new version (10.1.0) of Tamper Data has been released in order to address this issue.
Acknowledgements:
I would like to thank Tamper Data's author, Adam Judson, for his quick response and the efficient way in which he handled this security issue.